Losses from cybercrime has increased sharply as ransomware incidents soar, ‘cybercrime as a service’ provides greater access and new threats emerge, forcing banks to implement multilayered and stronger technology enabled IT risk and security frameworks.
October 12, 2018 | Neeti Aggarwal- The global cost of cybercrime has jumped to about $600 billion in 2017
- The incidents of ‘cybercrime as a service’ and botnet threats are rising
- Banks are adopting stronger threat intelligence with multilayered defence towards an integrated IT risk framework
As cybercriminals get more innovative and organised, and gain greater access to tools to attack the organisations with, the resulting costs from these crimes have escalated.
A study conducted by Center for Strategic and International Studies (CSIS) and McAfee recently estimated that the cybercrime cost to the world is close to $600 billion, or 0.8 percent of global GDP, which is up from their 2014 study that put global losses at about $445 billion, 0.62% of GDP. The cost varies across geographies with almost $158 billion in USA, a significant $140 billion in East Asia and Pacific and $11 billion in South Asia.
The report noted that with more than 6,000 online criminal marketplaces, ransomware and cybercrime-as-a-service are gaining popularity. The attacks have become more sophisticated, with flourishing markets offering a broad diversity of tools and services such as exploit kits, custom malware and botnet rentals.
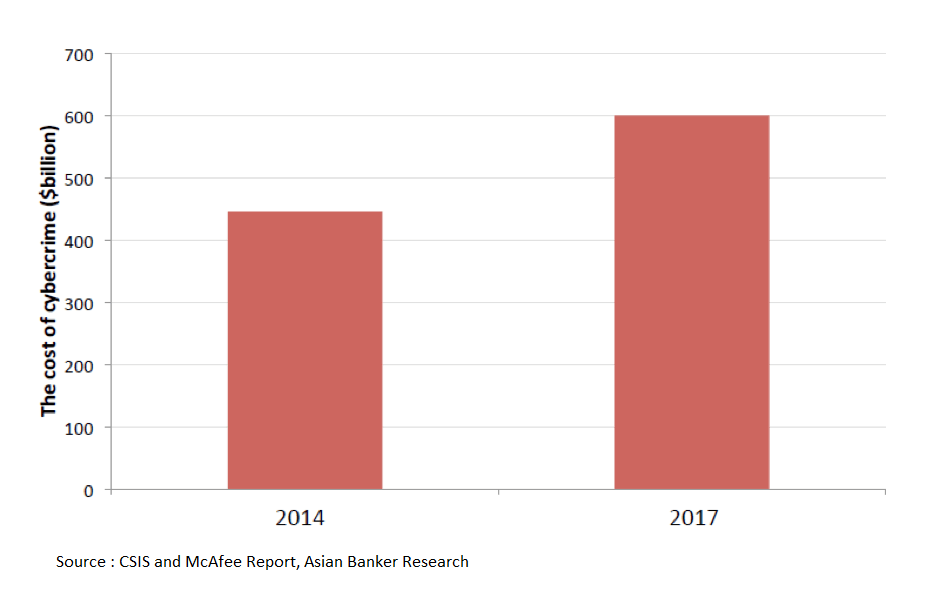
The rising cost of cybercrime
Figure 1: Cyber crime has increased the global losses
Emerging key trends in cybercrime
Ransomware and ‘cybercrime as a service’ threat get bigger: 2017 saw some unprecedented ransomware attacks like WannaCry and Petya that affected hundreds of thousands of people globally.
Talking about recent trends, David Allot, Director, cyber defense and solutions marketing, APAC, at McAfee said, “Firstly, ransomware, the fastest growing cybercrime used as a way of disrupting and sabotaging organisations has become a growing concern. This is now rising as on demand ‘cybercrime as a service’, wherein well-funded and capable hackers have essentially developed hacking tools for sale or rent. This has opened a door for many would-be cybercriminals because it is easy to access with little investment. A cybercriminal can spend as little as $60 a day to inflict damages of up to $720,000. The two other areas of concern are intellectual property theft and identity theft.”
IOT and botnets concerns grow: In an interconnected world of Internet of Things (IoT), the botnets may become a bigger concern.
“The marketplaces of the ‘Dark Web’ are increasingly offering ‘do it yourself’ (DIY) malware with more capabilities for sale, allowing anyone to participate in cybercrime. As the world adopts IoT, so have the cybercriminals. 2017 saw an increase in the number of IoT botnets, which will only get larger as more devices join the global network”, pointed Jerry Shiau, CIO, Taipei Fubon Bank.
“In addition, a new strain of high profile, globally scaled, and debilitating attacks appears to be government sponsored, specifically to achieve political goals” added Shiau.
Fileless malware incidents on the rise: The threats are evolving, becoming sophisticated and more difficult to manage with existing tools. Compared to traditional malware attacks where a hacker essentially conducts an attack by putting a file on the system, in a fileless malware, a file is no longer needed to initiate an attack as it leverages the memory of the targeted device. “Traditional cyber defense solutions may not be able to pick up fileless malware attacks, which have experienced an increase of 420% in the last year and likely to increase further”, opined Allot.
Cryptocurrency and cryptojacking frauds increase: Cryptocurrencies due to their distributed nature are increasingly used as a mode of payment in attacks like ransomware as they provide the requisite anonymity and protect criminals from easy identification.
“Moving forward, the involvement of cryptocurrency in cybercrime is only going to escalate. There are ongoing innovations around how criminals can leverage the Tor network, an open network that allows people to browse the web anonymously. This is particularly helpful for cybercriminals, who can use the Tor network to access dark web anonymously and carry out malicious activities”, Allot added.
Cryptojacking, where cybercriminals use tools such as malware for hacking and installing cryptocurrency mining tools in the systems of individuals and organisations to steal computing power, are rising rapidly. This stolen computing power is used to run algorithms to generate cryptocurrencies. McAfee Lab reported that there was a whopping 629% rise in ‘coinminer’ malware in the first quarter of 2018, compared to the last quarter of 2017.
Financial institutions need a multilayered security framework
With huge potential damages, not just monetary but also reputational, cybersecurity is now a paramount focus of banks. The CSIS report points that banks are spending three times more towards fighting cybercrime as compared to other businesses.
Rapidly evolving threats are forcing banks to explore new security controls, revise strategic approaches while installing new IT solutions. The institutions increasingly realise that a siloed approach will not be effective and the need for a bank-wide stronger IT risk management framework with senior management and board oversight, accompanied with a change in mindset and culture.
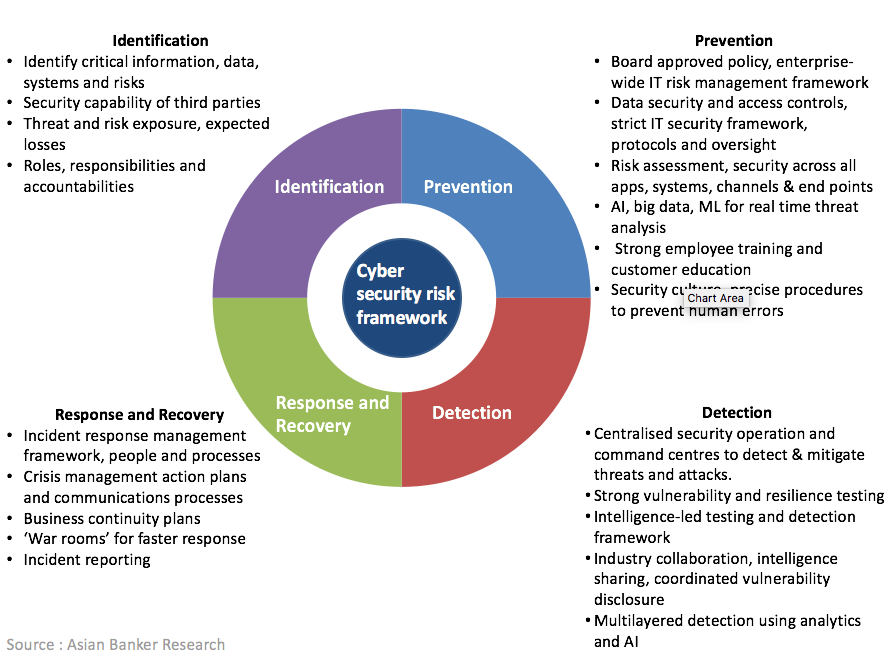
“Banks need a good framework of prevention, detection, reaction and recovery. They need prevention to a known risk, vulnerability access right management, but the key today is the detection and the reaction.” pointed Stéphane Nappo, global chief information security officer & board advisor, SociétéGénérale.
Banks need a stronger and integrated IT risk framework
Figure 2: Key elements of cybersecurity risk framework
Banks adopt technology innovation and threat intelligence for security
Attacks often exploit the gaps in traditional security approaches such as a lack of shared intelligence among the siloed security tools, insufficient automation in managing the security risks, and ability to address the threats in real time.
“We have focused towards finding good and reliable technology that can help us towards anti advanced persistent threats. We recently implemented the Information Security Management Platform that uniquely combines intelligent multi-vector attack detection, automates investigation, deep forensics, and actionable response in an integrated platform. This brings us shared intelligence and enables automated monitoring, behaviour analyses while triggering end point forensic and consolidated alerts for instant response” said Shiau, CIO, Taipei Fubon Bank.
The institutions are exploring emerging technologies that can connect the data points, information across systems enabling real time intelligence. “We are planning to introduce more Artificial Intelligence (AI) and machine learning solution to enhance the defense abilities of Information Security”, added Shiau, talking about their future investments.
Taipei Fubon Bank has implemented an “Information Security Management Platform” that can integrate intelligence on multi-vector attack detection with automated investigation, real time forensics, and actionable responses. It uses a machine-learning system for automated analysis and detection of the software which is targeting the system. The system monitors payloads, networks and all end-points, automatically detecting any attacks across the bank. The analysis is compiled into an incident report, which includes real time alerts, risk scores and recommendations for response. This helps the analysts better understand the threat landscape and enabled the bank to reduce thousands of alerts per day to a manageable number of incidents that needed action.
The response to cyber attacks is getting more integrated.
For instance, UnionBank of Philippines has established a 24x7 integrated operations centre for monitoring its services and cyber threats and ensuring fast response. This includes a network operations centre that has multiple dashboards to tracks the network, all website, the accessibility of bank’s services, response time to customers and business services management. Its security operation centre is focused on cyber security monitoring of its internal systems and any external threats. It has deployed a security information and event management (SIEM) system which creates visibility of the cyber environment and also the digital assets by centralising the collection and analysis of relevant data from multiple security sources and monitoring alerts in near real-time. It also implemented an enterprise fraud management system that combines data analytics and real-time alerts to further strengthen monitoring and detection. The centre generates cyber threat intelligence and is able to track any potential inbound attacks in real time and to block the cyber attacks based on their signature and known vulnerabilities. The bank also has a situation or war room, stationed along with the security operations centre which provides a stronger incident response.
Intrusion prevention and ensuring the resiliency of systems is at top of the list and banks are actively engaging with external agencies to test their systems.
“Cyber security as a big threat and one of our top priorities. Now with omni-channel and digital integration all our channels are open to this threat. Besides deploying new technology measures we are actively engaging external companies to do different security hack tests to ensure the robustness of security of our systems. In addition we are planning a security operations centre (SOC) towards end of this year”, said Priyantha Edirisinghe, Head of IT, People’s Bank, Sri Lanka.
Regulators are also prescribing testing of systems, Hong Kong Monetary Authority (HKMA) for instance prescribed a ‘Cyber Resilience Assessment Framework ‘that includes an inherent risk assessment, maturity assessment, and an intelligence-led cyber-attack simulation testing to ensure security.
With greater adoption of digital technologies and cloud, the data perimeter is disappearing while the number of end points is increasing. Attacks like Equifax, where data of 143 million customers was hacked, highlight the need for data security.
AI engines and machine learning based solutions can be used to sieve through the repository of digital data to identify potential threats and also to verify the customer identities. As the incidents of synthetic identity frauds rise, banks require stronger know your customer (KYC) initiatives accompanied with greater collaboration with credit bureaus and law enforcement agencies. Biometrics is also being increasingly explored for verification and controlling access.
Wells Fargo is using voice verification at its call centre and fingerprint and face recognition at its mobile app. It also started offering eye-recognition technology as a security measure to its corporate customers. Citi has also enabled voice recognition at its call centre. Maybank’s App has options for fingerprint, face and voice recognition for login while Shinhan Bank uses palm vein recognition at its digital kiosks.
Shared industry intelligence improves defense
Besides individual measures by institutions, greater collaboration with the industry, regulators and law enforcement agencies can strengthen real time intelligence and transparency that could play a key role in prevention and preparedness for timely response.
“In Netherlands, we put representatives from big banks, law enforcement and public prosecutor together and they discuss on a daily basis the attacks that have hit them and whenever it targets more than one of them, they can file a report together with a law enforcement agency. This has been working well as it provided a legal foundation for exchange of information” shared Roeland van Zeijst, Global cyber security strategist, and former digital crime officer, Interpol, Singapore
Such industry collaborative initiatives are being seen in other countries as well. For instance HKMA’s ‘Cyber Intelligence Sharing Platform’ seeks to provide an effective infrastructure for sharing intelligence on cyber-attacks; being set up by the HKMA together with the HK Association of Banks (HKAB) and ASTRI.
“One other idea that was proposed by our government and adopted by many organisations is “coordinated vulnerability disclosure”, wherein they invite and collaborate with young individuals who experiment, try to hack and identify leaks that need to be fixed, added Zeijst.
Humans remain a weak link
While the institutions deploy stronger technology systems and risk framework, the human element still remains a weak link that has led to many attacks.
“90% of cyber attacks are by human error – either by guilt or by fault, but the institutions continue to invest in IT and the people factor is often ignored. Institutions need to develop a positive security culture and complete the framework with precise procedures. The security needs to be planned before the project, with clear roles, access rights, data management and so forth, it has to be a continual development”, pointed Société Générale’s Stéphane Nappo.
The initiatives taken vary as some opt to use off-the-shelf software to automate the consolidation of data and certain manual checks to flag suspicious activity while other may use data science platforms that provide technological agility to build business rules and algorithms on the platform.
“Banks have been working on controlling what employees can access based on their levels of seniority and ensure that there would be no rooms for collusion”, said Sean Duca, regional chief security officer of Asia Pacific at Palo Alto Networks. “This goes back to one of the core tenets, where from a security standpoint you really need to have visibility. You really need to be able to see everything and understand: What is the user doing, what applications are they accessing, do they have the correct credentials, and not just simply rely on a username and password, how do we start to implement some extra levels of security,” he explained.
The outook
Cyber threats will continue to escalate and evolve as they become more organised and hacking tools and services become more readily available. Thus preparedness for an attack and ability to launch a quick recover and response would be critical for institutions.
“It is not a matter of ‘if ’ but ‘when’. Many companies have already been breached. Be prepared for the fact that it is going to happen, have a proper communication planning in place, have right people on board and be prepared for it. If you can only invest in one thing then it is “be prepared for it to happen”, pointed Ricardo Gonçalves, head of APAC intelligence, Barclays Group
Innovations in emerging technology such as AI and big data analytics can facilitate stronger intelligence for timely intervention and a stronger collaboration with fintechs should be explored for advanced threat analysis and detection. However, one needs to remember that no innovation or emerging technology is immune to cyber hacking. Banks will need to continually adapt, test and strengthen their systems while building defense through an integrated bank-wide risk management framework based on a consistent, overarching strategy.
Categories:
Keywords:Technology, Cybercrime, AI
Losses from cybercrime has increased sharply as ransomware incidents soar, ‘cybercrime as a service’ provides greater access and new threats emerge, forcing banks to implement multilayered and stronger technology enabled IT risk and security frameworks.
October 12, 2018 | Neeti Aggarwal- The global cost of cybercrime has jumped to about $600 billion in 2017
- The incidents of ‘cybercrime as a service’ and botnet threats are rising
- Banks are adopting stronger threat intelligence with multilayered defence towards an integrated IT risk framework
As cybercriminals get more innovative and organised, and gain greater access to tools to attack the organisations with, the resulting costs from these crimes have escalated.
A study conducted by Center for Strategic and International Studies (CSIS) and McAfee recently estimated that the cybercrime cost to the world is close to $600 billion, or 0.8 percent of global GDP, which is up from their 2014 study that put global losses at about $445 billion, 0.62% of GDP. The cost varies across geographies with almost $158 billion in USA, a significant $140 billion in East Asia and Pacific and $11 billion in South Asia.
The report noted that with more than 6,000 online criminal marketplaces, ransomware and cybercrime-as-a-service are gaining popularity. The attacks have become more sophisticated, with flourishing markets offering a broad diversity of tools and services such as exploit kits, custom malware and botnet rentals.
The rising cost of cybercrime
Figure 1: Cyber crime has increased the global losses
Emerging key trends in cybercrime
Ransomware and ‘cybercrime as a service’ threat get bigger: 2017 saw some unprecedented ransomware attacks like WannaCry and Petya that affected hundreds of thousands of people globally.
Talking about recent trends, David Allot, Director, cyber defense and solutions marketing, APAC, at McAfee said, “Firstly, ransomware, the fastest growing cybercrime used as a way of disrupting and sabotaging organisations has become a growing concern. This is now rising as on demand ‘cybercrime as a service’, wherein well-funded and capable hackers have essentially developed hacking tools for sale or rent. This has opened a door for many would-be cybercriminals because it is easy to access with little investment. A cybercriminal can spend as little as $60 a day to inflict damages of up to $720,000. The two other areas of concern are intellectual property theft and identity theft.”
IOT and botnets concerns grow: In an interconnected world of Internet of Things (IoT), the botnets may become a bigger concern.
“The marketplaces of the ‘Dark Web’ are increasingly offering ‘do it yourself’ (DIY) malware with more capabilities for sale, allowing anyone to participate in cybercrime. As the world adopts IoT, so have the cybercriminals. 2017 saw an increase in the number of IoT botnets, which will only get larger as more devices join the global network”, pointed Jerry Shiau, CIO, Taipei Fubon Bank.
“In addition, a new strain of high profile, globally scaled, and debilitating attacks appears to be government sponsored, specifically to achieve political goals” added Shiau.
Fileless malware incidents on the rise: The threats are evolving, becoming sophisticated and more difficult to manage with existing tools. Compared to traditional malware attacks where a hacker essentially conducts an attack by putting a file on the system, in a fileless malware, a file is no longer needed to initiate an attack as it leverages the memory of the targeted device. “Traditional cyber defense solutions may not be able to pick up fileless malware attacks, which have experienced an increase of 420% in the last year and likely to increase further”, opined Allot.
Cryptocurrency and cryptojacking frauds increase: Cryptocurrencies due to their distributed nature are increasingly used as a mode of payment in attacks like ransomware as they provide the requisite anonymity and protect criminals from easy identification.
“Moving forward, the involvement of cryptocurrency in cybercrime is only going to escalate. There are ongoing innovations around how criminals can leverage the Tor network, an open network that allows people to browse the web anonymously. This is particularly helpful for cybercriminals, who can use the Tor network to access dark web anonymously and carry out malicious activities”, Allot added.
Cryptojacking, where cybercriminals use tools such as malware for hacking and installing cryptocurrency mining tools in the systems of individuals and organisations to steal computing power, are rising rapidly. This stolen computing power is used to run algorithms to generate cryptocurrencies. McAfee Lab reported that there was a whopping 629% rise in ‘coinminer’ malware in the first quarter of 2018, compared to the last quarter of 2017.
Financial institutions need a multilayered security framework
With huge potential damages, not just monetary but also reputational, cybersecurity is now a paramount focus of banks. The CSIS report points that banks are spending three times more towards fighting cybercrime as compared to other businesses.
Rapidly evolving threats are forcing banks to explore new security controls, revise strategic approaches while installing new IT solutions. The institutions increasingly realise that a siloed approach will not be effective and the need for a bank-wide stronger IT risk management framework with senior management and board oversight, accompanied with a change in mindset and culture.
“Banks need a good framework of prevention, detection, reaction and recovery. They need prevention to a known risk, vulnerability access right management, but the key today is the detection and the reaction.” pointed Stéphane Nappo, global chief information security officer & board advisor, SociétéGénérale.
Banks need a stronger and integrated IT risk framework
Figure 2: Key elements of cybersecurity risk framework
Banks adopt technology innovation and threat intelligence for security
Attacks often exploit the gaps in traditional security approaches such as a lack of shared intelligence among the siloed security tools, insufficient automation in managing the security risks, and ability to address the threats in real time.
“We have focused towards finding good and reliable technology that can help us towards anti advanced persistent threats. We recently implemented the Information Security Management Platform that uniquely combines intelligent multi-vector attack detection, automates investigation, deep forensics, and actionable response in an integrated platform. This brings us shared intelligence and enables automated monitoring, behaviour analyses while triggering end point forensic and consolidated alerts for instant response” said Shiau, CIO, Taipei Fubon Bank.
The institutions are exploring emerging technologies that can connect the data points, information across systems enabling real time intelligence. “We are planning to introduce more Artificial Intelligence (AI) and machine learning solution to enhance the defense abilities of Information Security”, added Shiau, talking about their future investments.
Taipei Fubon Bank has implemented an “Information Security Management Platform” that can integrate intelligence on multi-vector attack detection with automated investigation, real time forensics, and actionable responses. It uses a machine-learning system for automated analysis and detection of the software which is targeting the system. The system monitors payloads, networks and all end-points, automatically detecting any attacks across the bank. The analysis is compiled into an incident report, which includes real time alerts, risk scores and recommendations for response. This helps the analysts better understand the threat landscape and enabled the bank to reduce thousands of alerts per day to a manageable number of incidents that needed action.
The response to cyber attacks is getting more integrated.
For instance, UnionBank of Philippines has established a 24x7 integrated operations centre for monitoring its services and cyber threats and ensuring fast response. This includes a network operations centre that has multiple dashboards to tracks the network, all website, the accessibility of bank’s services, response time to customers and business services management. Its security operation centre is focused on cyber security monitoring of its internal systems and any external threats. It has deployed a security information and event management (SIEM) system which creates visibility of the cyber environment and also the digital assets by centralising the collection and analysis of relevant data from multiple security sources and monitoring alerts in near real-time. It also implemented an enterprise fraud management system that combines data analytics and real-time alerts to further strengthen monitoring and detection. The centre generates cyber threat intelligence and is able to track any potential inbound attacks in real time and to block the cyber attacks based on their signature and known vulnerabilities. The bank also has a situation or war room, stationed along with the security operations centre which provides a stronger incident response.
Intrusion prevention and ensuring the resiliency of systems is at top of the list and banks are actively engaging with external agencies to test their systems.
“Cyber security as a big threat and one of our top priorities. Now with omni-channel and digital integration all our channels are open to this threat. Besides deploying new technology measures we are actively engaging external companies to do different security hack tests to ensure the robustness of security of our systems. In addition we are planning a security operations centre (SOC) towards end of this year”, said Priyantha Edirisinghe, Head of IT, People’s Bank, Sri Lanka.
Regulators are also prescribing testing of systems, Hong Kong Monetary Authority (HKMA) for instance prescribed a ‘Cyber Resilience Assessment Framework ‘that includes an inherent risk assessment, maturity assessment, and an intelligence-led cyber-attack simulation testing to ensure security.
With greater adoption of digital technologies and cloud, the data perimeter is disappearing while the number of end points is increasing. Attacks like Equifax, where data of 143 million customers was hacked, highlight the need for data security.
AI engines and machine learning based solutions can be used to sieve through the repository of digital data to identify potential threats and also to verify the customer identities. As the incidents of synthetic identity frauds rise, banks require stronger know your customer (KYC) initiatives accompanied with greater collaboration with credit bureaus and law enforcement agencies. Biometrics is also being increasingly explored for verification and controlling access.
Wells Fargo is using voice verification at its call centre and fingerprint and face recognition at its mobile app. It also started offering eye-recognition technology as a security measure to its corporate customers. Citi has also enabled voice recognition at its call centre. Maybank’s App has options for fingerprint, face and voice recognition for login while Shinhan Bank uses palm vein recognition at its digital kiosks.
Shared industry intelligence improves defense
Besides individual measures by institutions, greater collaboration with the industry, regulators and law enforcement agencies can strengthen real time intelligence and transparency that could play a key role in prevention and preparedness for timely response.
“In Netherlands, we put representatives from big banks, law enforcement and public prosecutor together and they discuss on a daily basis the attacks that have hit them and whenever it targets more than one of them, they can file a report together with a law enforcement agency. This has been working well as it provided a legal foundation for exchange of information” shared Roeland van Zeijst, Global cyber security strategist, and former digital crime officer, Interpol, Singapore
Such industry collaborative initiatives are being seen in other countries as well. For instance HKMA’s ‘Cyber Intelligence Sharing Platform’ seeks to provide an effective infrastructure for sharing intelligence on cyber-attacks; being set up by the HKMA together with the HK Association of Banks (HKAB) and ASTRI.
“One other idea that was proposed by our government and adopted by many organisations is “coordinated vulnerability disclosure”, wherein they invite and collaborate with young individuals who experiment, try to hack and identify leaks that need to be fixed, added Zeijst.
Humans remain a weak link
While the institutions deploy stronger technology systems and risk framework, the human element still remains a weak link that has led to many attacks.
“90% of cyber attacks are by human error – either by guilt or by fault, but the institutions continue to invest in IT and the people factor is often ignored. Institutions need to develop a positive security culture and complete the framework with precise procedures. The security needs to be planned before the project, with clear roles, access rights, data management and so forth, it has to be a continual development”, pointed Société Générale’s Stéphane Nappo.
The initiatives taken vary as some opt to use off-the-shelf software to automate the consolidation of data and certain manual checks to flag suspicious activity while other may use data science platforms that provide technological agility to build business rules and algorithms on the platform.
“Banks have been working on controlling what employees can access based on their levels of seniority and ensure that there would be no rooms for collusion”, said Sean Duca, regional chief security officer of Asia Pacific at Palo Alto Networks. “This goes back to one of the core tenets, where from a security standpoint you really need to have visibility. You really need to be able to see everything and understand: What is the user doing, what applications are they accessing, do they have the correct credentials, and not just simply rely on a username and password, how do we start to implement some extra levels of security,” he explained.
The outook
Cyber threats will continue to escalate and evolve as they become more organised and hacking tools and services become more readily available. Thus preparedness for an attack and ability to launch a quick recover and response would be critical for institutions.
“It is not a matter of ‘if ’ but ‘when’. Many companies have already been breached. Be prepared for the fact that it is going to happen, have a proper communication planning in place, have right people on board and be prepared for it. If you can only invest in one thing then it is “be prepared for it to happen”, pointed Ricardo Gonçalves, head of APAC intelligence, Barclays Group
Innovations in emerging technology such as AI and big data analytics can facilitate stronger intelligence for timely intervention and a stronger collaboration with fintechs should be explored for advanced threat analysis and detection. However, one needs to remember that no innovation or emerging technology is immune to cyber hacking. Banks will need to continually adapt, test and strengthen their systems while building defense through an integrated bank-wide risk management framework based on a consistent, overarching strategy.
Categories:
Keywords:Technology, Cybercrime, AI